获取 AWS 登录详细信息
如需使用 AWS 启用云,您需要在激活 Incredibuild Cloud 期间提供以下几个登录详细信息。
-
Role ARN– 新角色创建时自动生成的角色 Amazon 资源名称 (ARN)。有关 Amazon Resource Names (ARN) 的更多信息,请参阅 AWS 文档。
-
External ID – 您输入的外部 ID 将作为条件进入到新角色的 Trust Relationships设置中。有关 External ID 的更多信息,请参阅 AWS 文档。
要生成这些登录详细信息,您需要执行以下流程:
注意:仅具有 Administrator Access 策略和 Programmatic Access 类型的 IAM 用户需要进行这些流程。这些流程在 2021 年 11 月进行过验证,但在此之后 AWS 应用流程可能已发生变化。
创建 Custom AWS Policy
-
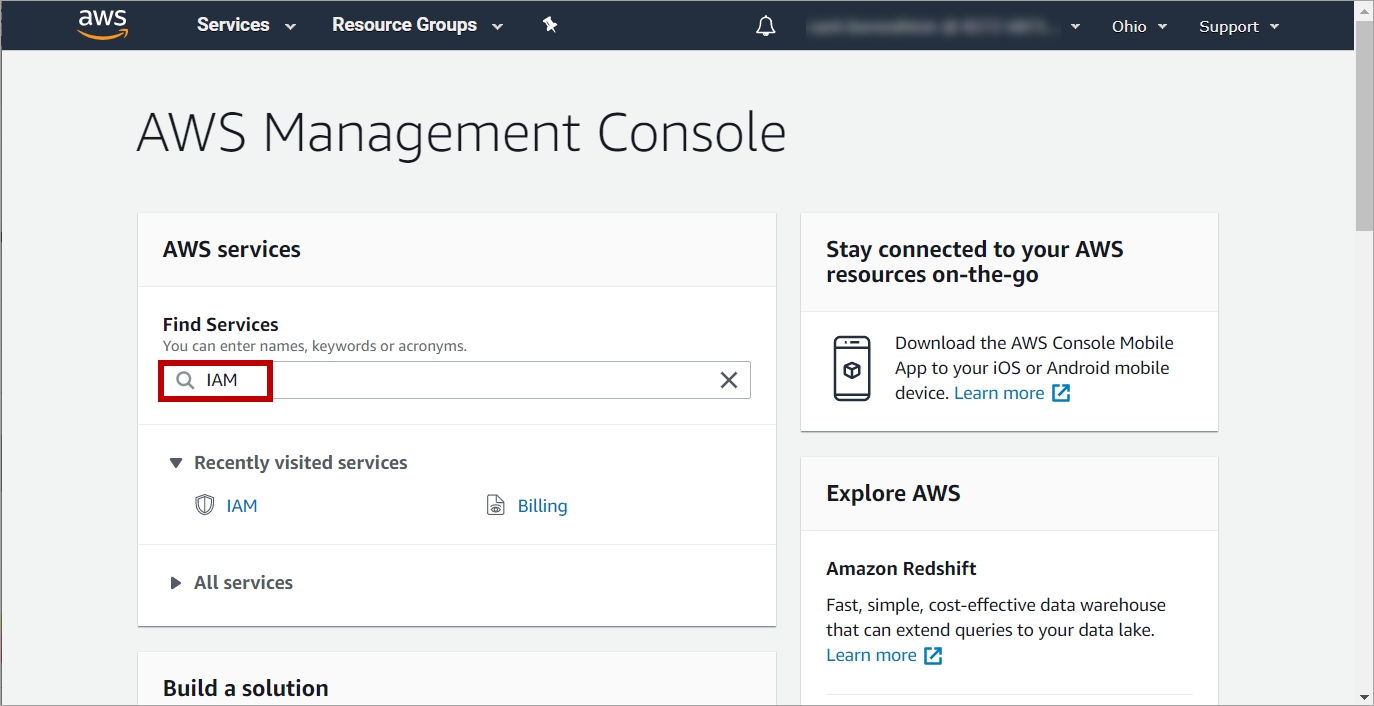
在 AWS Management Console 中的Find Services 框中输入:IAM:
-
在 IAM 页面中,点击 Policies 选项:
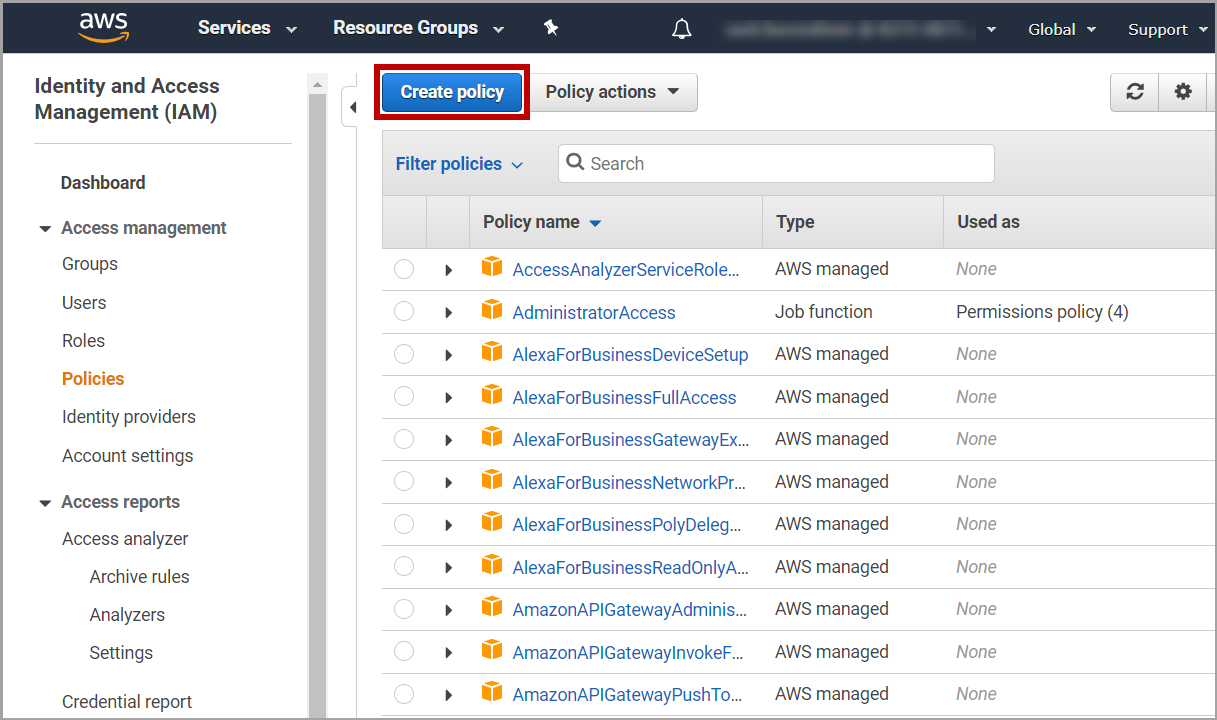
-
在Policies 页面中,点击 Create policy 按钮:
-
在第一个 Create Policy 页面中,点击 JSON 选项卡:
-
根据您的环境输入以下代码。
-
如果您想将自定义角色附加到您的云虚拟机,请使用下面的 “Custom VM Role” 选项,并指定您在 AWS 中创建的角色。您还需要在 Cloud Settings 中指定角色。
-
在隐私政策中,您必须用您的帐户详细信息替换一些代码。
-
如果您不确定使用哪一个,您应使用具有自定义虚拟机角色的公共网络策略。
-
如果您计划使用 Private Link,也可添加 ec2:DescribeVpcEndpoints 权限。
 无自定义虚拟机角色的公共网络策略
无自定义虚拟机角色的公共网络策略
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": [
"servicequotas:ListServices",
"ec2:AuthorizeSecurityGroupIngress",
"ec2:DeleteSubnet",
"ec2:DescribeInstances",
"ec2:RequestSpotInstances",
"ec2:CreateVpc",
"ec2:RequestSpotFleet",
"ec2:AttachInternetGateway",
"ec2:DescribeSpotInstanceRequests",
"servicequotas:GetServiceQuota",
"ec2:ModifySubnetAttribute",
"ec2:DescribeInternetGateways",
"ec2:ModifySpotFleetRequest",
"ec2:DescribeNetworkInterfaces",
"ec2:StartInstances",
"ec2:CreateRoute",
"ec2:CreateInternetGateway",
"ec2:CreateSecurityGroup",
"ec2:DeleteInternetGateway",
"ec2:ModifyInstanceAttribute",
"ec2:DescribeRouteTables",
"servicequotas:ListServiceQuotas",
"ec2:DescribeCapacityReservations",
"ec2:TerminateInstances",
"ec2:DescribeLaunchTemplates",
"ec2:CreateTags",
"ec2:RunInstances",
"ec2:CreateFleet",
"ec2:DetachInternetGateway",
"ec2:StopInstances",
"ec2:DescribeSecurityGroups",
"ec2:CreateLaunchTemplateVersion",
"ec2:RevokeSecurityGroupIngress",
"ec2:DescribeImages",
"ec2:CancelSpotInstanceRequests",
"ec2:CreateLaunchTemplate",
"ec2:DescribeSecurityGroupRules",
"ec2:DescribeVpcs",
"ec2:DeleteSecurityGroup",
"ec2:DeleteVpc",
"ec2:CreateSubnet",
"ec2:DescribeSubnets",
"ec2:DescribeAvailabilityZones",
"ec2:DescribeInstanceTypeOfferings"
],
"Resource": "*"
},
{
"Effect": "Allow",
"Action": "iam:CreateServiceLinkedRole",
"Resource": "arn:aws:iam::*:role/aws-service-role/spot.amazonaws.com/*",
"Condition": {
"StringLike": {
"iam:AWSServiceName": "spot.amazonaws.com"
}
}
},
{
"Sid": "VisualEditor1",
"Effect": "Allow",
"Action": "iam:CreateServiceLinkedRole",
"Resource": "arn:aws:iam::*:role/aws-service-role/ec2fleet.amazonaws.com/*",
"Condition": {
"StringLike": {
"iam:AWSServiceName": "ec2fleet.amazonaws.com"
}
}
},
{
"Sid": "VisualEditor2",
"Effect": "Allow",
"Action": [
"iam:AttachRolePolicy",
"iam:PutRolePolicy"
],
"Resource": "arn:aws:iam::*:role/aws-service-role/ec2fleet.amazonaws.com/*"
}
]
} 无自定义虚拟机角色的私人网络策略
无自定义虚拟机角色的私人网络策略
将 "youraccountnumber" 和 "vpcid" 替换为您的帐户信息。
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "Subnets",
"Effect": "Allow",
"Action": [
"ec2:DescribeSubnets"
],
"Resource": "*"
},
{
"Sid": "Vpc",
"Effect": "Allow",
"Action": [
"ec2:DescribeInternetGateways",
"ec2:DescribeVpcs"
],
"Resource": "*"
},
{
"Sid": "Images",
"Effect": "Allow",
"Action": [
"ec2:DescribeImages"
],
"Resource": "*"
},
{
"Sid": "Tags",
"Effect": "Allow",
"Action": [
"ec2:CreateTags"
],
"Resource": "*"
},
{
"Sid": "LaunchTemplatesRead",
"Effect": "Allow",
"Action": [
"ec2:DescribeLaunchTemplates"
],
"Resource": "*"
},
{
"Sid": "LaunchTemplatesCreate",
"Effect": "Allow",
"Action": [
"ec2:CreateLaunchTemplate"
],
"Resource": "*"
},
{
"Sid": "LaunchTemplatesUpdate",
"Effect": "Allow",
"Action": [
"ec2:CreateLaunchTemplateVersion"
],
"Resource": "*"
},
{
"Sid": "InstancesRead",
"Effect": "Allow",
"Action": [
"ec2:DescribeCapacityReservations",
"ec2:DescribeInstances",
"ec2:DescribeSpotInstanceRequests",
"ec2:DescribeAvailabilityZones",
"ec2:DescribeInstanceTypeOfferings"
],
"Resource": "*"
},
{
"Sid": "InstancesCreate",
"Effect": "Allow",
"Action": [
"ec2:RunInstances",
"ec2:CreateFleet",
"ec2:RequestSpotFleet",
"ec2:RequestSpotInstances"
],
"Resource": "*"
},
{
"Sid": "InstancesWrite",
"Effect": "Allow",
"Action": [
"ec2:StartInstances",
"ec2:StopInstances",
"ec2:TerminateInstances",
"ec2:ModifyInstanceAttribute",
"ec2:ModifySpotFleetRequest",
"ec2:CancelSpotInstanceRequests"
],
"Resource": "*",
"Condition": {
"StringLike": {
"ec2:ResourceTag/resourceGroup": "*cloud-rg"
}
}
},
{
"Sid": "SecurityGroupsRead",
"Effect": "Allow",
"Action": [
"ec2:DescribeSecurityGroups"
],
"Resource": "*"
},
{
"Sid": "SecurityGroupCreate",
"Effect": "Allow",
"Action": [
"ec2:CreateSecurityGroup"
],
"Resource": [
"arn:aws:ec2:*:<youraccountnumber>:vpc/<yourvpcid>",
"arn:aws:ec2:*:<youraccountnumber>:security-group/*"
]
},
{
"Sid": "SecurityGroupDelete",
"Effect": "Allow",
"Action": [
"ec2:DeleteSecurityGroup"
],
"Resource": "*",
"Condition": {
"StringLike": {
"ec2:ResourceTag/resourceGroup": "*cloud-rg"
}
}
},
{
"Sid": "SecurityGroupsRulesRead",
"Effect": "Allow",
"Action": [
"ec2:DescribeSecurityGroupRules"
],
"Resource": "*"
},
{
"Sid": "SecurityGroupsRulesWrite",
"Effect": "Allow",
"Action": [
"ec2:AuthorizeSecurityGroupIngress",
"ec2:RevokeSecurityGroupIngress"
],
"Resource": "*",
"Condition": {
"StringLike": {
"ec2:ResourceTag/resourceGroup": "*cloud-rg"
}
}
},
{
"Sid": "Quotas",
"Effect": "Allow",
"Action": [
"servicequotas:ListServices",
"servicequotas:GetServiceQuota",
"servicequotas:ListServiceQuotas"
],
"Resource": "*"
},
{
"Sid": "SpotServiceLinkedRole",
"Effect": "Allow",
"Action": "iam:CreateServiceLinkedRole",
"Resource": "arn:aws:iam::*:role/aws-service-role/spot.amazonaws.com/*",
"Condition": {
"StringLike": {
"iam:AWSServiceName": "spot.amazonaws.com"
}
}
},
{
"Sid": "Ec2FleetServiceLinkedRole",
"Effect": "Allow",
"Action": "iam:CreateServiceLinkedRole",
"Resource": "arn:aws:iam::*:role/aws-service-role/ec2fleet.amazonaws.com/*",
"Condition": {
"StringLike": {
"iam:AWSServiceName": "ec2fleet.amazonaws.com"
}
}
}
]
} 具有自定义虚拟机角色的公共网络策略
具有自定义虚拟机角色的公共网络策略
将 "Account-Id"、"RoleName1" 和 "RoleName2" 替换为您的帐户 ID 和自定义虚拟机角色名称。您可以指定一个角色或任意多个角色。
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": [
"servicequotas:ListServices",
"ec2:AuthorizeSecurityGroupIngress",
"ec2:DeleteSubnet",
"ec2:DescribeInstances",
"ec2:RequestSpotInstances",
"ec2:CreateVpc",
"ec2:RequestSpotFleet",
"ec2:AttachInternetGateway",
"ec2:DescribeSpotInstanceRequests",
"servicequotas:GetServiceQuota",
"ec2:ModifySubnetAttribute",
"ec2:DescribeInternetGateways",
"ec2:ModifySpotFleetRequest",
"ec2:DescribeNetworkInterfaces",
"ec2:StartInstances",
"ec2:CreateRoute",
"ec2:CreateInternetGateway",
"ec2:CreateSecurityGroup",
"ec2:DeleteInternetGateway",
"ec2:ModifyInstanceAttribute",
"ec2:DescribeRouteTables",
"servicequotas:ListServiceQuotas",
"ec2:DescribeCapacityReservations",
"ec2:TerminateInstances",
"ec2:DescribeLaunchTemplates",
"ec2:CreateTags",
"ec2:RunInstances",
"ec2:CreateFleet",
"ec2:DetachInternetGateway",
"ec2:StopInstances",
"ec2:DescribeSecurityGroups",
"ec2:CreateLaunchTemplateVersion",
"ec2:RevokeSecurityGroupIngress",
"ec2:DescribeImages",
"ec2:CancelSpotInstanceRequests",
"ec2:CreateLaunchTemplate",
"ec2:DescribeSecurityGroupRules",
"ec2:DescribeVpcs",
"ec2:DeleteSecurityGroup",
"ec2:DeleteVpc",
"ec2:CreateSubnet",
"ec2:DescribeIamInstanceProfileAssociations",
"ec2:DescribeSubnets",
"ec2:DescribeAvailabilityZones",
"ec2:DescribeInstanceTypeOfferings"
],
"Resource": "*"
},
{
"Effect": "Allow",
"Action": "iam:CreateServiceLinkedRole",
"Resource": "arn:aws:iam::*:role/aws-service-role/spot.amazonaws.com/*",
"Condition": {
"StringLike": {
"iam:AWSServiceName": "spot.amazonaws.com"
}
}
},
{
"Sid": "VisualEditor1",
"Effect": "Allow",
"Action": "iam:CreateServiceLinkedRole",
"Resource": "arn:aws:iam::*:role/aws-service-role/ec2fleet.amazonaws.com/*",
"Condition": {
"StringLike": {
"iam:AWSServiceName": "ec2fleet.amazonaws.com"
}
}
},
{
"Sid": "VisualEditor2",
"Effect": "Allow",
"Action": [
"iam:AttachRolePolicy",
"iam:PutRolePolicy"
],
"Resource": "arn:aws:iam::*:role/aws-service-role/ec2fleet.amazonaws.com/*"
},
{
"Sid": "VisualEditor3",
"Effect": "Allow",
"Action": [
"iam:GetRole",
"iam:PassRole"
],
"Resource": [
"arn:aws:iam::<Account-Id>:role/<RoleName1>",
"arn:aws:iam::<Account-Id>:role/<RoleName2>"
]
},
{
"Sid": "VisualEditor4",
"Effect": "Allow",
"Action": [
"ec2:DisassociateIamInstanceProfile",
"ec2:AssociateIamInstanceProfile"
],
"Resource": "",
"Condition": {
"StringEquals": {
"ec2:ResourceTag/incredibuild": "1"
}
}
}
]
} 具有自定义虚拟机角色的私人网络策略
具有自定义虚拟机角色的私人网络策略
将 "youraccountnumber" 和 "vpcid" 替换为您的帐户信息。
将 "Account-Id"、"RoleName1" 和 "RoleName2" 替换为您的帐户 ID 和自定义虚拟机角色名称。您可以指定一个角色或任意多个角色。
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "Subnets",
"Effect": "Allow",
"Action": [
"ec2:DescribeSubnets"
],
"Resource": "*"
},
{
"Sid": "Vpc",
"Effect": "Allow",
"Action": [
"ec2:DescribeInternetGateways",
"ec2:DescribeVpcs"
],
"Resource": "*"
},
{
"Sid": "Images",
"Effect": "Allow",
"Action": [
"ec2:DescribeImages"
],
"Resource": "*"
},
{
"Sid": "Tags",
"Effect": "Allow",
"Action": [
"ec2:CreateTags"
],
"Resource": "*"
},
{
"Sid": "LaunchTemplatesRead",
"Effect": "Allow",
"Action": [
"ec2:DescribeLaunchTemplates"
],
"Resource": "*"
},
{
"Sid": "LaunchTemplatesCreate",
"Effect": "Allow",
"Action": [
"ec2:CreateLaunchTemplate"
],
"Resource": "*"
},
{
"Sid": "LaunchTemplatesUpdate",
"Effect": "Allow",
"Action": [
"ec2:CreateLaunchTemplateVersion"
],
"Resource": "*"
},
{
"Sid": "InstancesRead",
"Effect": "Allow",
"Action": [
"ec2:DescribeCapacityReservations",
"ec2:DescribeInstances",
"ec2:DescribeSpotInstanceRequests",
"ec2:DescribeAvailabilityZones",
"ec2:DescribeInstanceTypeOfferings"
],
"Resource": "*"
},
{
"Sid": "InstancesCreate",
"Effect": "Allow",
"Action": [
"ec2:RunInstances",
"ec2:CreateFleet",
"ec2:RequestSpotFleet",
"ec2:RequestSpotInstances"
],
"Resource": "*"
},
{
"Sid": "InstancesWrite",
"Effect": "Allow",
"Action": [
"ec2:StartInstances",
"ec2:StopInstances",
"ec2:TerminateInstances",
"ec2:ModifyInstanceAttribute",
"ec2:ModifySpotFleetRequest",
"ec2:CancelSpotInstanceRequests"
],
"Resource": "*",
"Condition": {
"StringLike": {
"ec2:ResourceTag/resourceGroup": "*cloud-rg"
}
}
},
{
"Sid": "SecurityGroupsRead",
"Effect": "Allow",
"Action": [
"ec2:DescribeSecurityGroups"
],
"Resource": "*"
},
{
"Sid": "SecurityGroupCreate",
"Effect": "Allow",
"Action": [
"ec2:CreateSecurityGroup"
],
"Resource": [
"arn:aws:ec2:*:<youraccountnumber>:vpc/<yourvpcid>",
"arn:aws:ec2:*:<youraccountnumber>:security-group/*"
]
},
{
"Sid": "SecurityGroupDelete",
"Effect": "Allow",
"Action": [
"ec2:DeleteSecurityGroup"
],
"Resource": "*",
"Condition": {
"StringLike": {
"ec2:ResourceTag/resourceGroup": "*cloud-rg"
}
}
},
{
"Sid": "SecurityGroupsRulesRead",
"Effect": "Allow",
"Action": [
"ec2:DescribeSecurityGroupRules"
],
"Resource": "*"
},
{
"Sid": "SecurityGroupsRulesWrite",
"Effect": "Allow",
"Action": [
"ec2:AuthorizeSecurityGroupIngress",
"ec2:RevokeSecurityGroupIngress"
],
"Resource": "*",
"Condition": {
"StringLike": {
"ec2:ResourceTag/resourceGroup": "*cloud-rg"
}
}
},
{
"Sid": "Quotas",
"Effect": "Allow",
"Action": [
"servicequotas:ListServices",
"servicequotas:GetServiceQuota",
"servicequotas:ListServiceQuotas"
],
"Resource": "*"
},
{
"Sid": "SpotServiceLinkedRole",
"Effect": "Allow",
"Action": "iam:CreateServiceLinkedRole",
"Resource": "arn:aws:iam::*:role/aws-service-role/spot.amazonaws.com/*",
"Condition": {
"StringLike": {
"iam:AWSServiceName": "spot.amazonaws.com"
}
}
},
{
"Sid": "Ec2FleetServiceLinkedRole",
"Effect": "Allow",
"Action": "iam:CreateServiceLinkedRole",
"Resource": "arn:aws:iam::*:role/aws-service-role/ec2fleet.amazonaws.com/*",
"Condition": {
"StringLike": {
"iam:AWSServiceName": "ec2fleet.amazonaws.com"
}
}
},
{
"Sid": "GetAndPassRole",
"Effect": "Allow",
"Action": [
"iam:GetRole",
"iam:PassRole"
],
"Resource": [
"arn:aws:iam::<Account-Id>:role/<RoleName1>",
"arn:aws:iam::<Account-Id>:role/<RoleName2>"
]
},
{
"Sid": "AssociateAndDisassociateIamProfile",
"Effect": "Allow",
"Action": [
"ec2:DisassociateIamInstanceProfile",
"ec2:AssociateIamInstanceProfile"
],
"Resource": "",
"Condition": {
"StringEquals": {
"ec2:ResourceTag/incredibuild": "1"
}
}
},
{
"Sid": "IamInstanceProfileRulesRead",
"Effect": "Allow",
"Action": [
"ec2:DescribeIamInstanceProfileAssociations"
],
"Resource": "*"
}
]
} -
-
通过定义名称并点击 Create Policy 来完成政策。在后面的步骤中,您将需要使用该名称。
创建 Custom AWS Role
-
转到 Roles > Create Role。
-
在第一页中,选择 AWS service 作为实体类型,选择 EC2 作为常见用例。
-
在第二页中,使用 Filter policies 框查找您之前创建的自定义策略并点击其复选框。
-
[可选] 在第三页中,您可以为正在创建的新角色添加标签。
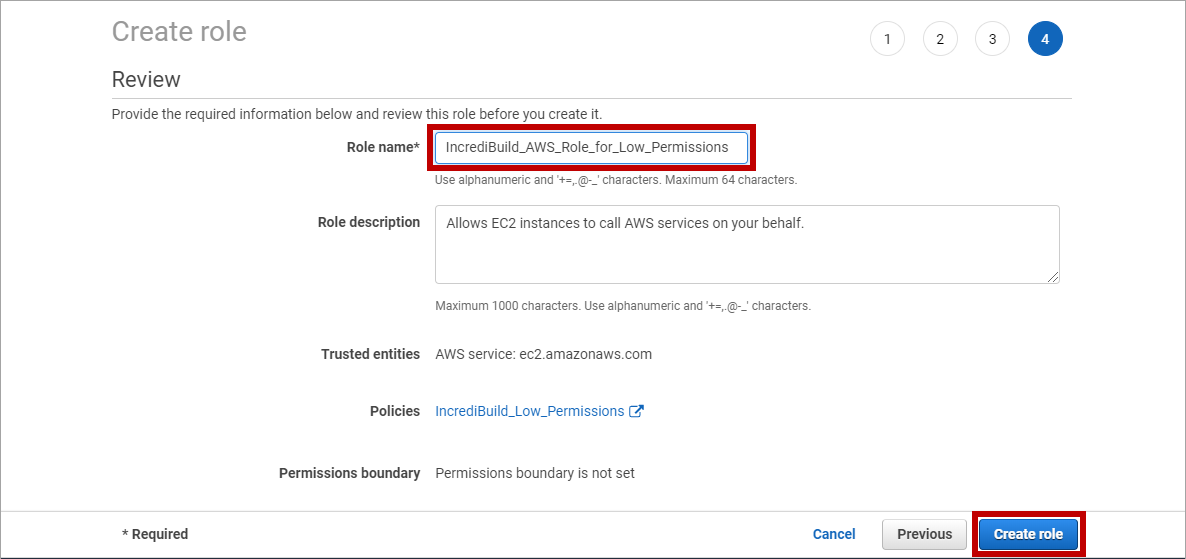
-
在第四页中,输入新角色名称并点击 Create role。
-
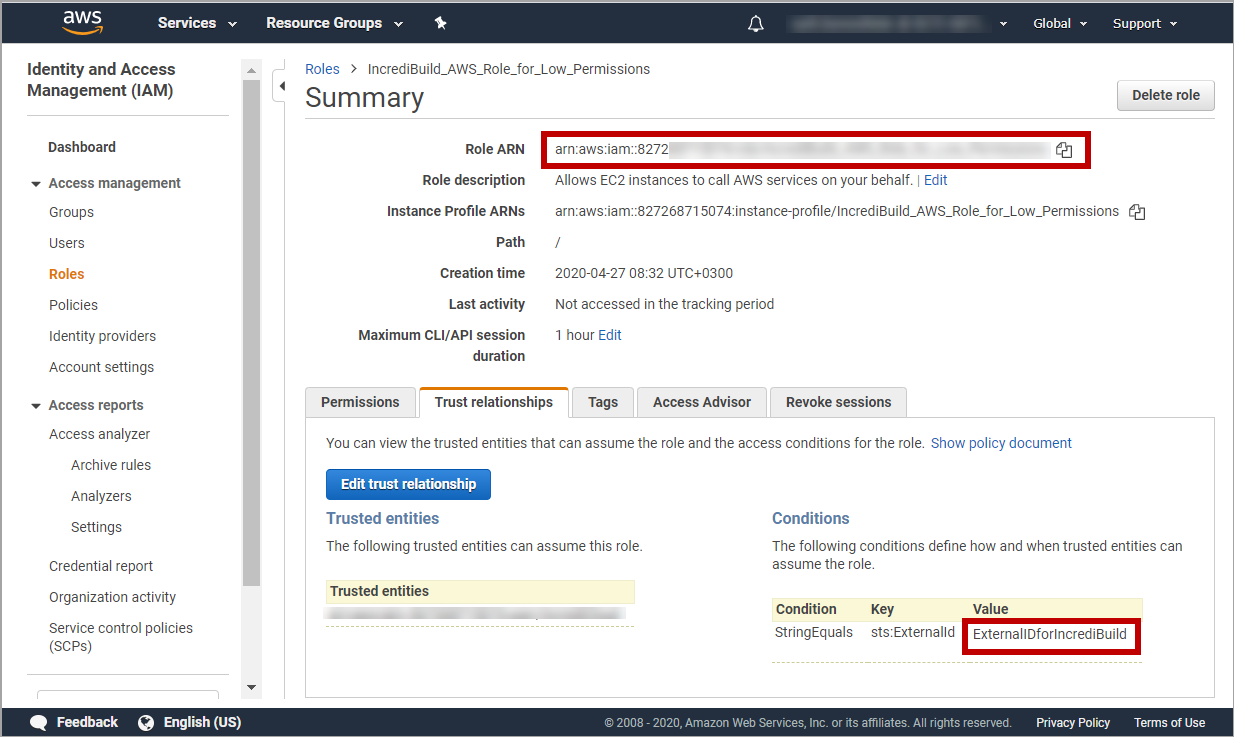
在Roles页面中找到新创建的角色。然后选中其复选框并点击以打开它:
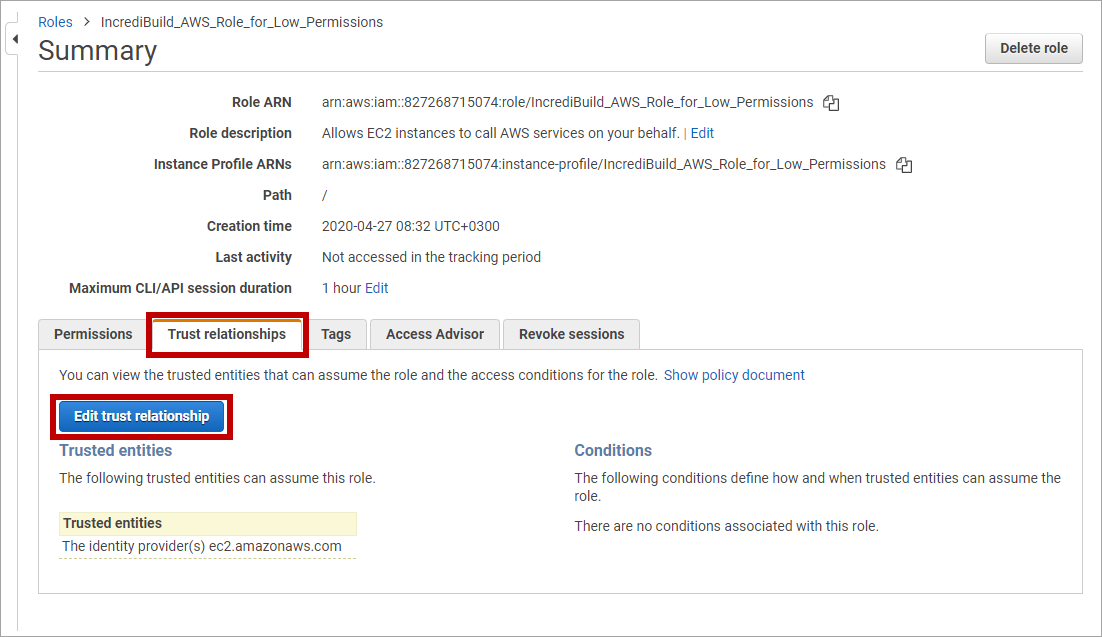
-
在新角色的Summary 页面中,点击 Trust relationships选项卡。然后点击Edit trust relationship 按钮:
-
在 Edit Trust Relationship 页面中,删除现有内容并将其替换为以下代码:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::827268715074:user/incrediCloud" },
"Action": "sts:AssumeRole",
"Condition": {
"StringEquals": {
"sts:ExternalId": "<New_String_for_Your_External_ID>" }
}
}
]
}
请输入不带特殊字符的唯一字符串来代替 "New_String_for_Your_External_ID"。您需要在激活期间将其提供给 Incredibuild。
-
在 Policy Document 窗格中输入了您的唯一外部 ID 后,点击 Update Trust Policy 按钮。您将返回所创建角色的 Summary 页面。在此Summary 页面中,您可以找到以较低权限激活 Incredibuild Cloud 所需的登录详细信息: